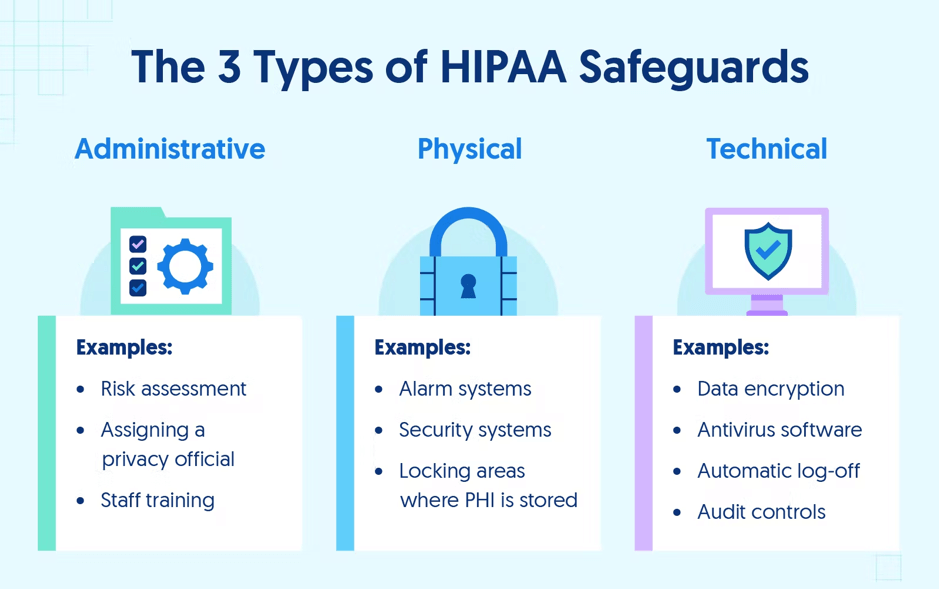
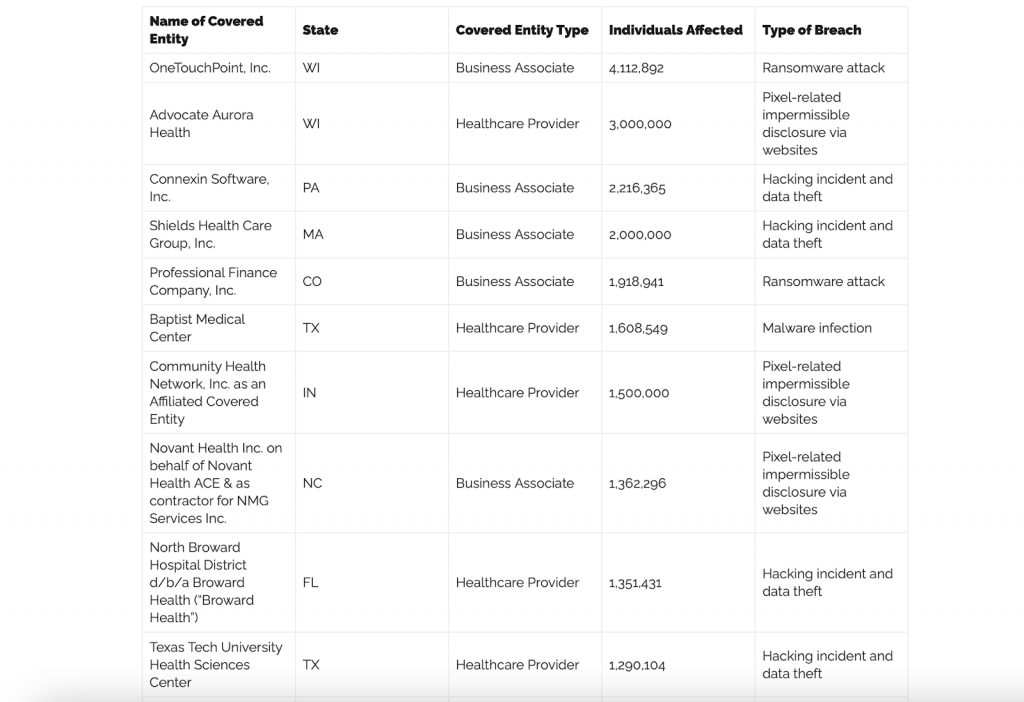
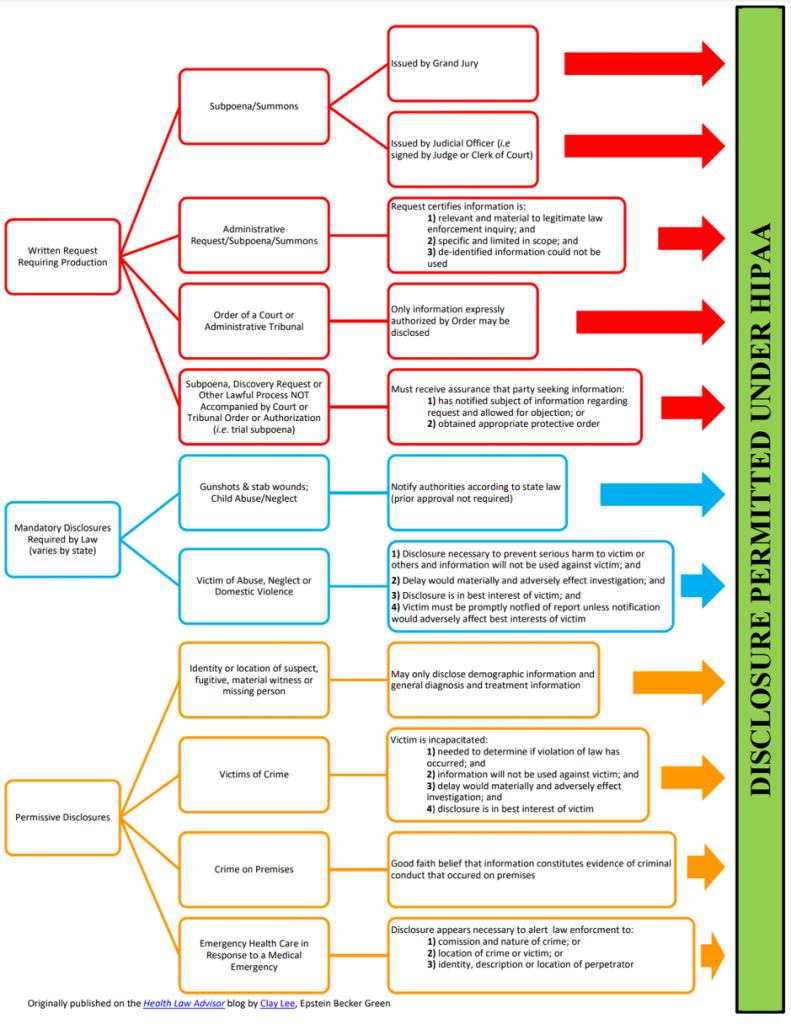
- What qualifies as protected health information (PHI) under HIPAA?
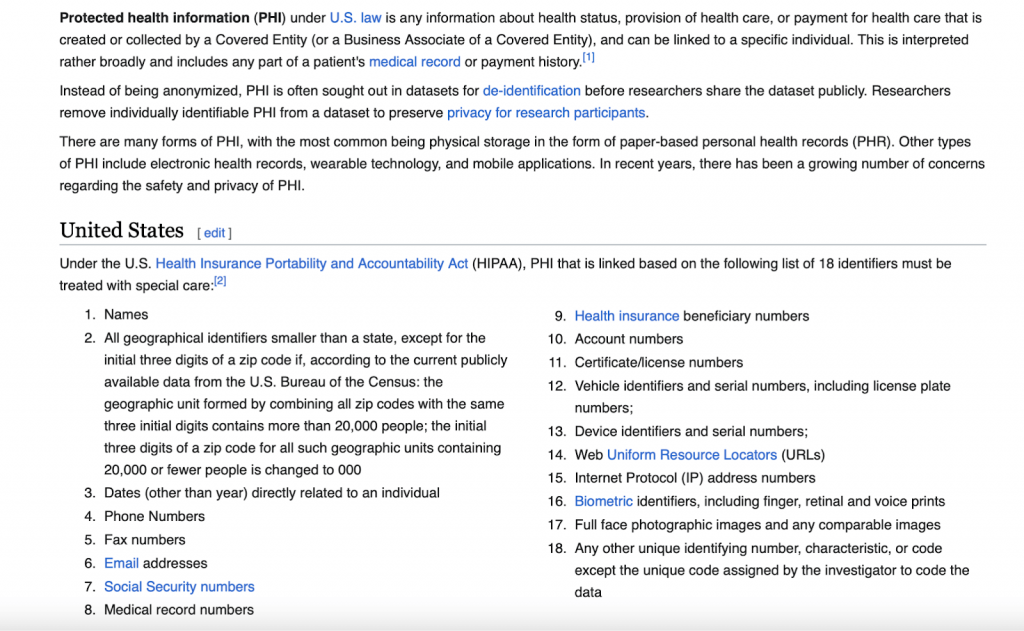
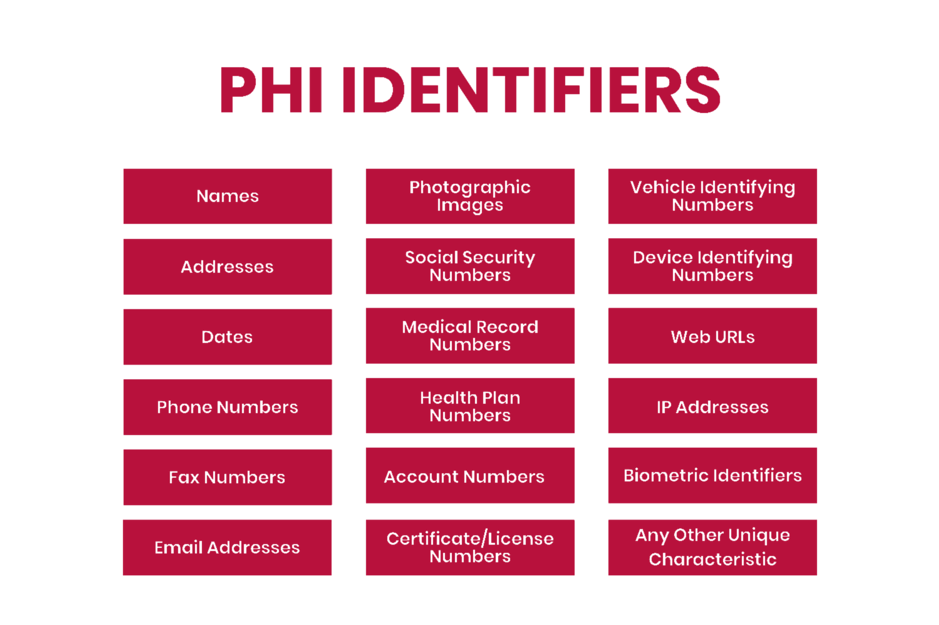
PHI is any individually identifiable health information that is created, received, stored, or transmitted by a covered entity or business associate. This includes information such as a person's name, address, birth date, medical history, test results, and other health information that can be used to identify an individual. PHI can be in any form, including electronic, paper, or oral communication.
- Is it permissible for healthcare providers to allow members of the media, including film crews, into treatment areas of their facilities without obtaining prior written authorization?No way. They are not allowed to let media personnel, including film crews, into areas of their facilities where patients' private health information (PHI) could be seen, heard, or accessed. That's right - written permission is needed from each individual whose PHI will be accessible to the media, whether it's in written, electronic, oral, or another visual or audio form. Now, there are some rare situations where HIPAA rules allow PHI sharing with the media without prior authorization from the patient. But these cases are very limited and carefully outlined in the rules. So, in general, your private data should stay private and protected from prying eyes!
- Does the HIPAA Privacy Rule cover genetic information?The answer is a resounding yes! Genetic information falls under the category of health information protected by the Privacy Rule, just like any other health-related data. However, for it to be considered protected, it must meet the definition of protected health information - which means it must be identifiable to an individual and be kept by a covered healthcare provider, health plan, or healthcare clearinghouse. So rest assured, your genetic info is safe and sounds under the HIPAA Privacy Rule!
- AI SOLUTIONS
- Services
DevOps as a ServiceDevOps on autopilot
CTO as a ServiceStregthen your team
Software testingEnsure software quality
Discovery phasePlan your priduct from a to z
Cloud ServicesGeneral information about healthcare cloud services
Google Cloud ServicesEnsuring confidentiality when working with medical systems
AWS Cloud ServicesServices specially designed for the healthcare industry
Microsoft Cloud ServicesPlatform processing, analyzing and sharing medical data
- Industries
- About
- Blog
- Portfolio