- What is Encryption?
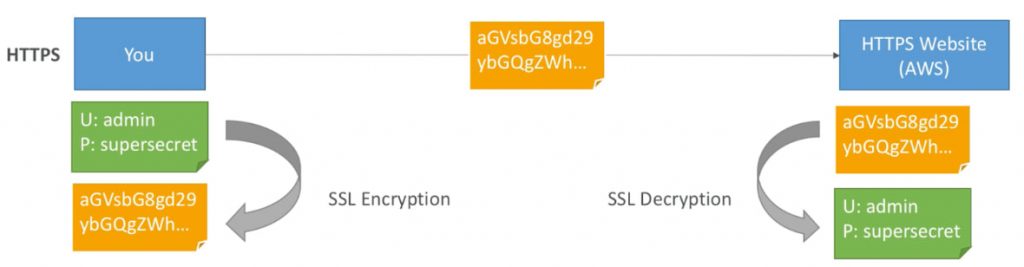
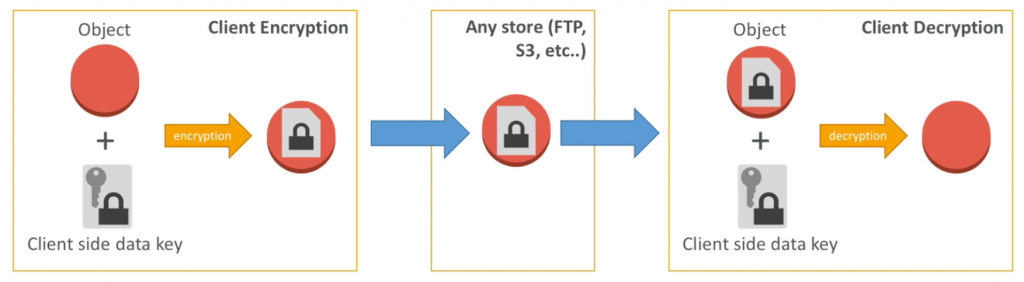
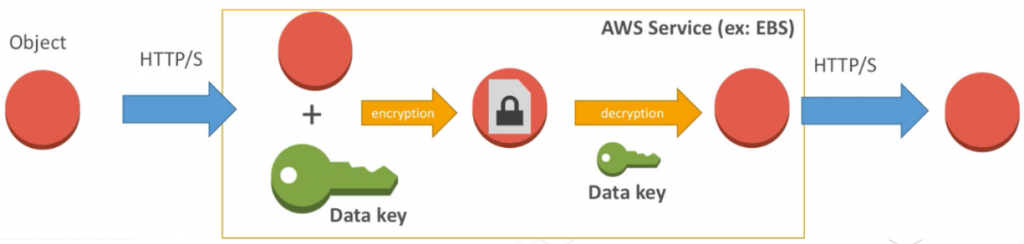
It is the process of transforming data into an unreadable format so that it can only be read by someone with the decryption key.
- What are AWS encryption tools?
- AWS Key Management Service (KMS);
- AWS CloudHSM;
- AWS Certificate Manager;
- Amazon S3 Server-Side Encryption;
- AWS Transit Gateway Network Manager;
- AWS CloudTrail.
- What are AWS encryption best practices?
- Implement server-side encryption;
- Enable multi-factor authentication;
- Use the least privilege access;
- Enable logging and auditing;
- Regularly rotate encryption keys.
- AI SOLUTIONS
- Services
DevOps as a ServiceDevOps on autopilot
CTO as a ServiceStregthen your team
Software testingEnsure software quality
Discovery phasePlan your priduct from a to z
Cloud ServicesGeneral information about healthcare cloud services
Google Cloud ServicesEnsuring confidentiality when working with medical systems
AWS Cloud ServicesServices specially designed for the healthcare industry
Microsoft Cloud ServicesPlatform processing, analyzing and sharing medical data
- Industries
- About
- Blog
- Portfolio