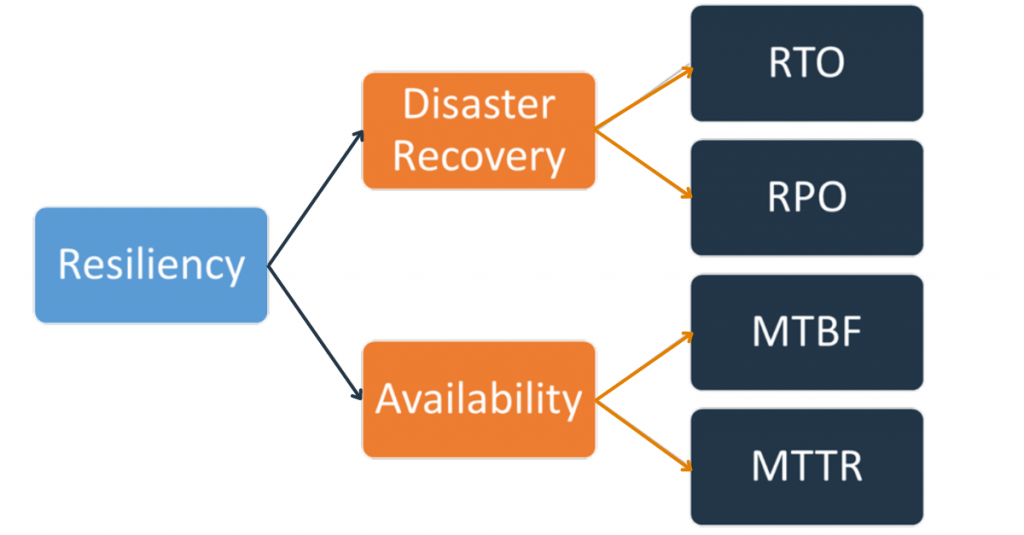
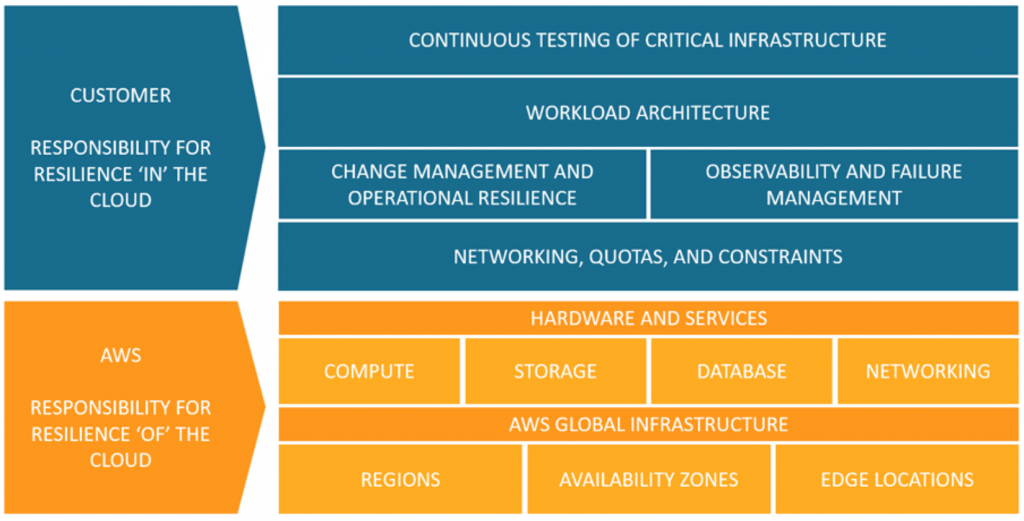
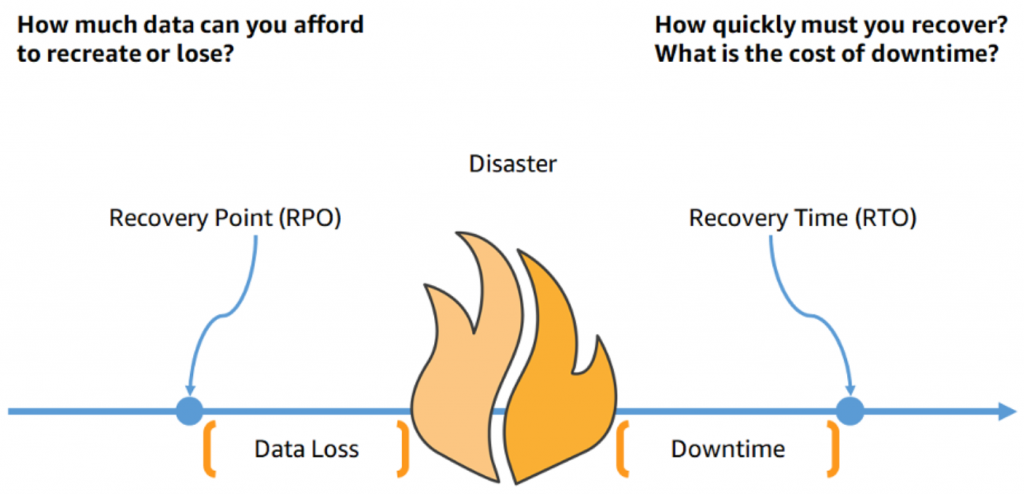
- How does disaster recovery work on AWS Cloud?
AWS offers various services and tools that facilitate disaster recovery, such as Amazon S3 for data storage, Amazon EC2 for compute resources, and AWS CloudFormation for infrastructure orchestration.
- Can I achieve near-zero downtime with disaster recovery on AWS Cloud?
Yes, AWS provides several features and services that allow you to achieve near-zero downtime during a disaster. For example, AWS Elastic Load Balancing, Amazon Route 53, and AWS Auto Scaling.
- Does disaster recovery on AWS Cloud support different types of workloads?
Yes, AWS supports a wide range of workloads, including mission-critical enterprise applications, web applications, databases, and virtual desktops.
- How can I ensure the security of my disaster recovery environment on AWS Cloud?
AWS provides a secure foundation with features such as identity and access management (IAM), encryption at rest and in transit, network isolation, and security monitoring.
- AI SOLUTIONS
- Services
DevOps as a ServiceDevOps on autopilot
CTO as a ServiceStregthen your team
Software testingEnsure software quality
Discovery phasePlan your priduct from a to z
Cloud ServicesGeneral information about healthcare cloud services
Google Cloud ServicesEnsuring confidentiality when working with medical systems
AWS Cloud ServicesServices specially designed for the healthcare industry
Microsoft Cloud ServicesPlatform processing, analyzing and sharing medical data
- Industries
- About
- Blog
- Portfolio