Data has become a powerful component for businesses in the current digital age, and its protection is fundamental.
The General Data Protection Regulation (GDPR) is a set of laws designed to protect the privacy and personal data of EU citizens. If your company operates in the EU, you need to ensure that your architecture is GDPR compliant.
So, how to be GDPR compliant? In this article, we’ll explore some best practices for achieving this important goal using cloud infrastructure Amazon Web Services (AWS)!
The GDPR applies to all processing of personal data either by organizations that have an establishment in the EU or EU supervisory authorities who can issue fines of up to EUR 20 million, or 4% of annual worldwide turnover, whichever is higher, for a breach of the GDPR.
Let’s talk about AWS solutions and models that can help you comply with GDPR.
Shared Responsibility Model Security and Compliance is a shared responsibility between AWS and the customer when the customers move their computer systems and data to the cloud. For abstracted services, such as Amazon S3 and Amazon DynamoDB AWS is also responsible for the security of the operating system and platform.
There are Tools for Data Access Controls
- With the AWS Security Token Service, you may generate and give trusted users temporary security credentials. And there are a few differences: short-term use can be configured for a duration of up to 12 hours, and temporary security credentials are produced dynamically and given to the user after request.
- To deploy customized Access to your AWS Resources, you can provide distinct users with varying levels of authority for supplies.
- For extra security, you can add Multi-Factor-Authentication to your AWS account and to IAM users.
- As for AWS Identity and Access Management, a root user generates automatically when you create an AWS account. This account should not be used for regular work, instead, it should only be used to initially create additional roles and users and perform any necessary administrative duties.
- As a user, you can specify the limits of access to local services and maintain ownership of your material with the aid of AWS. Without your permission, AWS does not access, store or use any of your content.
- Amazon Cognito will help you to add user login and access control features to your web applications and mobile apps as it provides a secure user directory. Use MFA to protect the user’s identity.
Solutions for Compliance in Monitoring and Logging
Article 30 of the GDPR states that “…each controller and, where applicable, the controller’s representative, shall maintain a record of processing activities under its responsibility”.
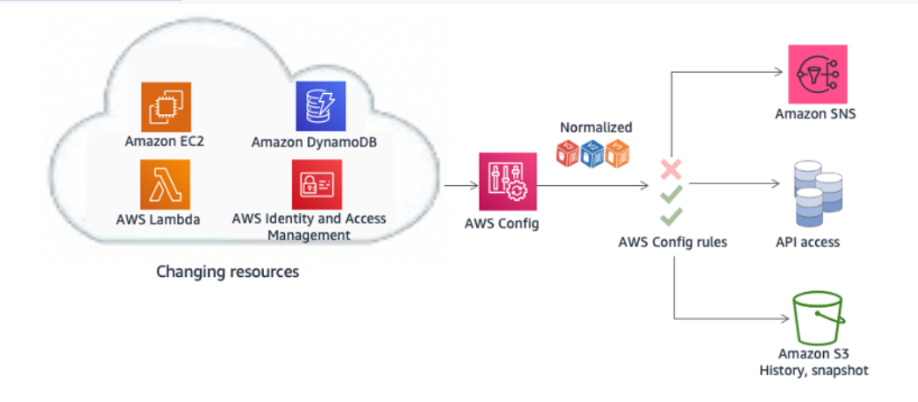
- AWS Config provides a detailed view of the configuration of many types of AWS resources. You can understand how the relationships and configurations have changed over time by looking at how the resources are related to one another and how they were previously set up.
With AWS Config, you can do the following:
— Evaluate your AWS resource configurations to verify the settings are correct.
— Get a snapshot of the current configurations of the supported resources that are associated with your AWS Account.
— Get configurations of one or more resources that exist in your account;
— Get historical configurations of one or more resources;
— Get a notification when a resource is created, modified, or deleted;
— See relationships between resources. For example, find all resources that use a particular security group.
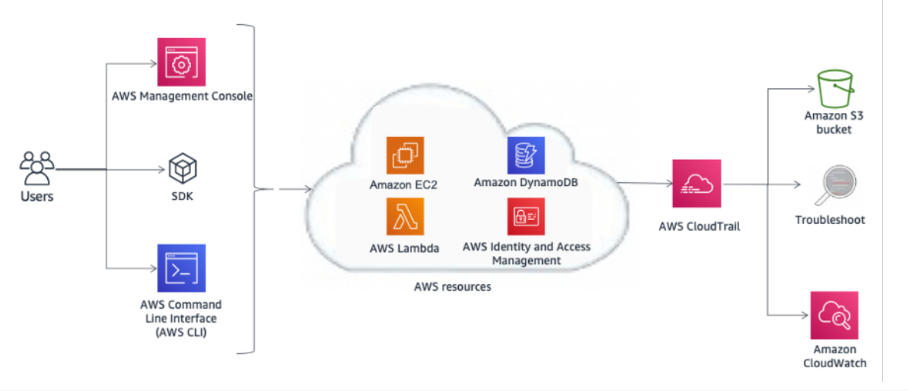
- You can keep an eye on activity related to your AWS account with Amazon CloudTrail. Your account’s history of Amazon API calls, including those made through the AWS Management Console, AWS SDKs, command-line tools, and more advanced AWS services, is recorded.
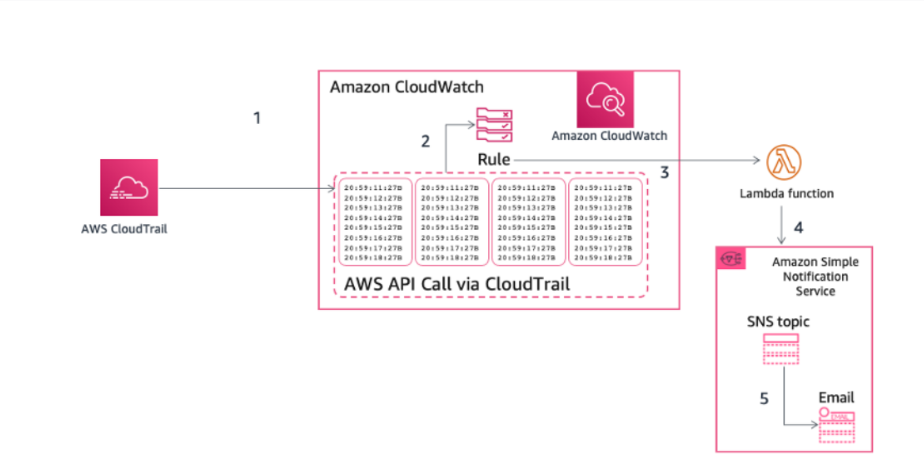
Moreover, preconfigured CloudWatch events may be triggered by AWS CloudTrail logs. These events can be used for corrective actions or to alert people or systems that an event has happened. For example, you can construct a CloudWatch Event rule to keep an eye on activity on your Amazon EC2 instances. The rule activates an Amazon Lambda function, which sends an email notification to the administrator about the event if a specific activity occurs on the EC2 instance and the event is recorded in the logs.
- You may monitor, keep, and access your log files from Amazon EC2 instances, AWS CloudTrail, Route 53, and other sources with CloudWatch Logs.
Logs information includes, for example:
— Granular logging of access to Amazon S3 objects;
— Detailed information about flows in the network through VPC-Flow Logs;
— Rule-based configuration verification and actions with AWS Config rules;
— Filtering and monitoring of HTTP access to applications with web application firewall (WAF) function in CloudFront.
- AWS provides Amazon Macie to assist customers in identifying and safeguarding their sensitive data at scale. It is a data security and privacy service that searches S3 buckets for personal information and protects it using pattern matching and machine learning models for the identification of Personally Identifying Information (PII). Macie is capable of detecting PII such as complete name, email address, birth date, NIN, taxpayer identity number, and more.
Watch our live stream on YouTube to learn more!
Security Management Requirements
Many organizations have challenges related to visibility and centralized management of their environments. Lack of knowledge, combined with decentralized and security processes, can make your environment vulnerable.
- AWS Control Tower provides a method to set up and govern a new, secure, multi-account AWS environment.
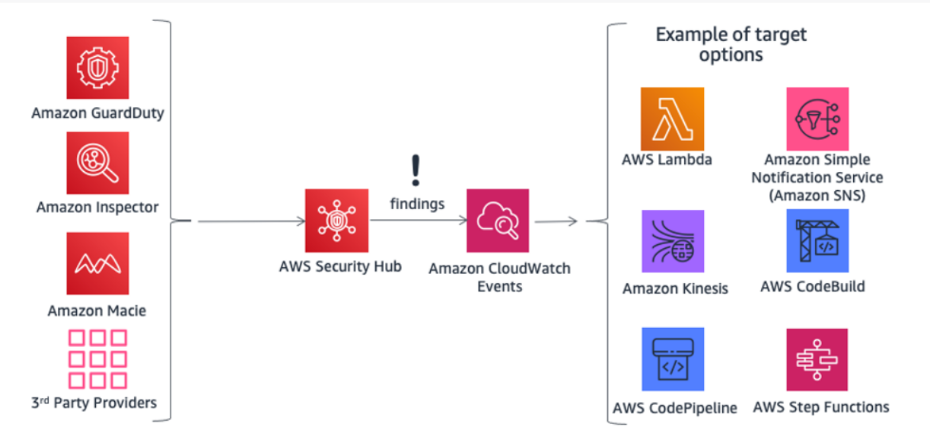
- AWS Security Hub centralizes and prioritizes security and compliance findings from across AWS accounts and services, such as Amazon GuardDuty and Amazon Inspector, and can be integrated with security software from third-party partners.
- Amazon GuardDuty is an intelligent threat detection service that can help customers more accurately and easily monitor and protect their AWS accounts, workloads, and data stored in Amazon S3.
- Amazon Inspector is an automated security assessment service that helps improve the security and compliance of applications deployed on Amazon EC2 instances. Applications are automatically evaluated by Amazon Inspector for exposure, vulnerabilities, and deviations.
- Amazon CloudWatch Events enables you to set up your AWS account to send events to other AWS accounts, or to become a receiver for events from other accounts or organizations.
Data Protection on AWS
Article 32 of the GDPR requires that organizations must “…implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk, including …the pseudonymisation and encryption of personal data…”.
- Encrypting Data at Rest is vital for regulatory compliance and data protection. It helps to ensure that sensitive data saved on disks is not readable by any user or application without a valid key.
- AWS strongly recommends Encrypting Data in Transit from one system to another, including resources within and outside of AWS.
- AWS offers various Encryption Tools to help protect your data stored and processed.
— AWS Key Management Service (AWS KMS) is an AWS-managed service that generates and manages both root keys and data keys;
— AWS CloudHSM provides HSMs that are FIPS 140-2 Level 3 validated. They securely store a variety of your self-managed cryptographic keys, including KMS keys and data keys;
— AWS Encryption SDK provides a client-side encryption library for implementing encryption and decryption operations on all types of data;
— Amazon DynamoDB Encryption Client provides a client-side encryption library for encrypting data tables before sending them to a database service.

In final
A combination of technical and administrative steps is needed to create an architecture that is GDPR-compliant on AWS. With the support of our ZenBit Tech team, you can put strong access safeguards in place, encrypt sensitive data, and keep a constant eye out for security risks.
Certainly, Amazon offers a variety of services that can assist you in becoming compliant, but we can ensure that your architecture is built and run in compliance!
- FAQ
Those who process data solely for domestic or personal purposes are exempt from the GDPR's provisions.
But, we should see some cases where a person processes data for another reason and could receive a GDPR fine.
- For example, if the individual is self-employed or a person is a sole trader, the possibility of receiving GDPR penalties exists for sure.
- A data privacy law has been violated by the person individually and that simply depends on how the law has been chosen to be applied in the country in which you conduct business.
A standard set of data security regulations was established throughout the EU in 2018 with the implementation of the General Data Protection Regulation (GDPR).
A comprehensive data privacy law with the goal of giving people more control over their personal data is known as the GDPR. Regardless of where the organization is located, it applies to all organizations that gather, handle or retain the personal data of people living in the EU.






